Can you surf the internet anonymously these days? The Tor project, which offers the Tor browser, promises strong privacy protection. In addition to the browser, it offers its own server infrastructure and even its own encrypted address (.onion) for websites.
The Tor project, despite its controversial reputation, is largely government-funded. This is one of the curiosities of a project that is repeatedly in the focus of secret services and investigative authorities due to cybercriminal activities. The Tor browser is often the last resort in authoritarian regimes to share information or evade internet censorship with possible criminal prosecution. Finally, normal Internet users who simply want to surf the Internet anonymously also use the Tor browser. Anonymous means of communication can also be important for press work and for anonymous whistleblowers. But first things first. The history and function of the Tor browser are not only exciting, but also ambivalent.
The idea and function behind the Tor browser
Tor’s origins date back to 1995. Three researchers, David Goldschlag, Michael Reed and Paul Syverson from the Naval Research Lab (NRL) looked at anonymous internet connections. The scientists at the American military research laboratory called their idea for anonymization “onion routing”. Like an onion, data passes through different layers until it becomes untraceable. To do this, Internet traffic is rerouted in a peer-to-peer network and passed around randomly until it leaves the network and arrives at its destination. Peer-to-peer stands for a computer network in which the computers communicate with each other equally.
Research on the Onion network was initially funded only by the NRL and Defense Advanced Research Projects Agency (DARPA) to allow military and intelligence personnel to work covertly online. The increasing dependency of state authorities on communication in the public Internet infrastructure made state employees vulnerable.
Originally cover for military and intelligence operations
When a spy wanted to collect publicly available information in another country, they usually left behind digital traces. Even an undercover spy in a foreign country could be exposed at any time if he wanted to get in touch with the CIA, for example. According to investigative journalist Yasha Levine, when a country’s Internet connection is under constant surveillance, it couldn’t simply pull up an intelligence site. This is where the original onion routing came in, it was intended to cover government operations.
This original military research and use of onion routing is puzzling. Because the Tor browser is best known because it is also used to access the dark web. The dark web is a hidden part of the web space that cannot be reached with common browsers. Darknet sites require special browsers, including the Tor browser. One of the inventors of Tor technology, Michael Reed, explains that the Tor browser has long been used for other, sometimes criminal, purposes:
“Of course we knew there would be other unavoidable uses for the technology, but that was irrelevant to the problem we were trying to solve. And if these uses would give us more cover traffic to better hide what we wanted to use the network for, so much the better (…)”
Yasha Levine | Pando.com | Pando Quarterly Summer 2014
Also read: How exactly does the dark web work?
The Onion routing is taking shape
In the 2000s, the NRL’s Paul Syverson stayed with the project. Two new fresh graduates from the Massachusetts Institute of Technology (MIT) were added at the same time. MIT is one of the top universities in the USA and is particularly renowned in the technical field. Roger Dingledine and Nick Mathewson continued to work on the NRL’s onion routing project. While not formally employed by a military naval research laboratory, they had contracts with DARPA and the NRP-backed research center – The Center for High Assurance Computer Systems (CHACS). Thus, the research on the Tor project was still funded by government agencies and research centers.
The Tor project got its name from Dingledine, so Tor stands for “The Onion Routing”. Thus the onion network was born. The onion adorns the Tor browser as a logo to this day.
Tor browser becomes popular among activists
Over the years, the Tor browser grew in popularity and many privacy activists and tech-savvy people joined it. In 2006, the project was incorporated into the independent, non-profit organization The Tor Project, Inc. She should be collaborating on the open-source project, where the source code is open for everyone to review.
The principle of entering the network via a Tor node (nodes) and exiting anonymously via an exit node was also very successful. Each node randomly passes the internet data to other Tor nodes on the network, covering up traces of the original internet access. Despite repressive Internet surveillance in authoritarian regimes, more and more people have been able to operate successfully with Tor. In this way, blocked social media channels and critical information can also be accessed, even if they are officially blocked by authorities. And, of course, cybercriminals were also beginning to take an interest in the technology. Not least because of this, the Tor browser is the focus of investigations by authorities and secret services. The Federal Intelligence Service (BND) even worked together with the American National Security Agency (NSA) to launch attacks on the Tor network. The aim was to unmask Tor users.
According to whistleblower Edward Snowden, secret services such as the NSA had little success monitoring the Tor network’s data traffic. Its success is based on the mass of Tor nodes used. However, the whole network can only function securely if enough volunteers provide Tor nodes. That is why the Tor network is always dependent on donations and voluntary work. It turned out that a particularly large number of users of the Tor network also come from authoritarian regimes such as Iran, because censorship and repression are particularly high there. The Tor browser is also used to circumvent government censorship. But how does the originally military background fit together?
Why is the US government funding the Tor network?
If the Tor browser is a safe tool for anonymization, why is the US government largely funding the project to this day? This is particularly bizarre because the American secret service NSA has been trying to specifically track down and monitor Tor users for years.
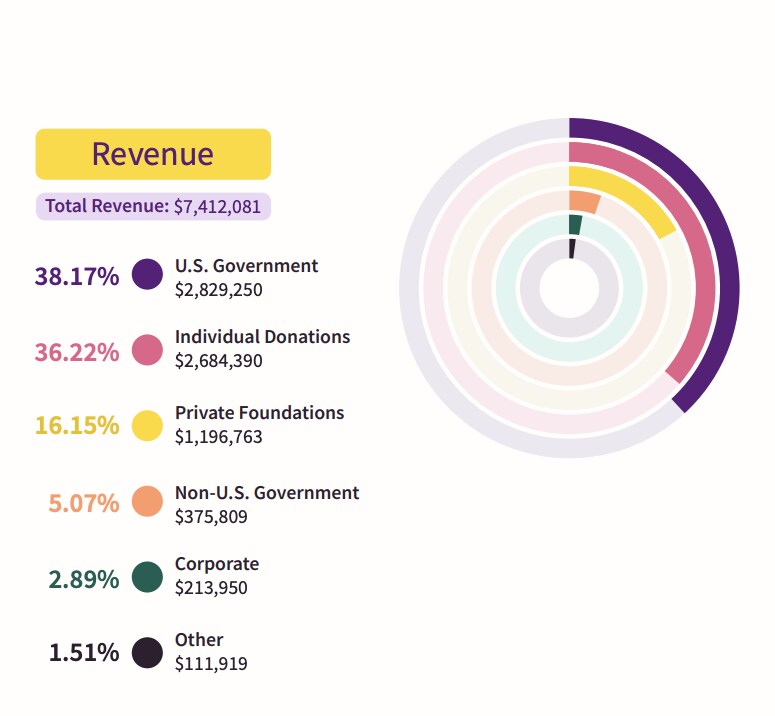
In 2020-2021, 38 percent of the Tor budget came from the US government. The Tor project has been trying to prevent this dependency for years and is increasingly relying on private ones Donate. In 2015, the proportion of funds that clearly came from US government funds was 63 percent. Together with other state funds, about 85 percent of the funds from state budgets amounted to. At least the proportion has been reduced somewhat to date. But why do governments fund such a project at all? On the one hand, this is due to various research funds that flow from different pots. On the other hand, investigative journalist Levine also sees a benefit for state authorities when various groups use Tor.
Diverse user groups necessary for anonymity
A system that provides technical anonymity is not sufficient if it is used exclusively by the military and secret services. Tor must therefore be used by diverse groups: activists, students, corporate researchers, soccer moms, journalists, drug dealers, hackers, cybercriminals, foreign agents, terrorists — the more diverse the group, the better a state agent can hide, Levin explains.
Syverson confirmed this assumption in a 2014 interview with Bloomberg. Regarding the funding of Tor research by the NRL and thus by the US Navy, he spoke of the need to separate Tor from naval research:
“If you have a system that’s just a Navy system, obviously everything that pops out of it is Navy. You need a network that also carries traffic for other people.”
Yasha Levine | Pando.com | Pando Quarterly Summer 2014
The journalist Levin even assumes that marketing the Tor browser in a “consumer version” is just as important. That’s enough volunteers to run a Tor node. This was the only way to create a large crowdsourcing network consisting of thousands of helpers.
This is what Tor pioneer Dingledine said at the 2004 Wizard OS conference in Germany:
“The United States government cannot just run an anonymization system for everyone and then use it only for themselves. Because every time a connection comes out of there, people say, ‘Oh, it’s another CIA agent.’ If that’s the only people using the network.”
Yasha Levine | Pando.com | Pando Quarterly Summer 2014
Indeed, in late 2004, the US Navy cut most of its Tor funding and released an open source license. Everyone could now view the source code and contribute to it. The project was briefly taken over by the Electronic Frontier Foundation (EFF), a non-governmental organization dedicated to protecting fundamental rights in the information age.
Independent further development of the Tor project
This created an anonymization tool that has enough internet traffic and is also partly supported by volunteers. Both parts benefit from it. Both activists and government agencies, if they really use the Tor browser. It remains questionable whether this is the only reason why the Tor project still exists in its current form. Because Tor has always had problems with users using the browser for cybercrime.
However, an unrelenting battle has also broken out as to how Internet traffic can be monitored and restricted in the future. The fact is, even if the Tor network still receives a lot of state money, it has of course emancipated itself and is one of the most interesting projects for anonymous surfing on the Internet. The history of Tor is therefore very ambiguous, but it is also demonstrably an independent open source project. Possible government backdoors for spying in the program code are thus theoretically recognizable.
Also interesting: Deep Web – the invisible side of the internet
Is the Tor browser anonymous on the internet?
The question of whether you are really anonymous with the Tor browser is difficult to answer. The fact is that the network depends on volunteer operators of Tor nodes that randomly move internet data back and forth. Of particular importance are the Tor nodes where data enters and exits (e.g., exit nodes). This could be a weak point in the network. In theory, if a certain number of Tor nodes are monitored, traffic within the Tor network can also be monitored. There are always limits to anonymity.
